Exploring the Top Cybersecurity Threats Facing the Internet Today
In the ever-evolving landscape of cyberspace, cybersecurity threats have become more sophisticated, pervasive, and challenging to mitigate. From data breaches to ransomware attacks, the digital realm is fraught with dangers that can compromise sensitive information, disrupt services, and wreak havoc on individuals and organizations alike. In this comprehensive guide, we’ll delve into the top cybersecurity threats facing the internet today and examine their impacts, techniques, and preventive measures.
1. Malware

Malware remains one of the most prevalent and versatile cyber threats. It encompasses a broad range of malicious software designed to infiltrate, damage, or gain unauthorized access to computer systems. From viruses and worms to Trojans and spyware, malware can spread through various vectors, including email attachments, infected websites, and removable media.
Techniques:
- Phishing: Cybercriminals use deceptive emails or messages to trick users into downloading malware.
- Drive-by Downloads: Malicious code is automatically downloaded onto a user’s device when visiting a compromised website.
- Fileless Malware: Exploits vulnerabilities in software or the operating system to execute malicious code without leaving a footprint on the hard drive.
Impact:
- Data Theft: Malware can steal sensitive information such as login credentials, financial details, and personal records.
- System Disruption: It can cause system slowdowns, crashes, or complete loss of functionality.
- Ransomware: Malware that encrypts files and demands payment for decryption, posing a significant threat to businesses and individuals.
Prevention:
- Antivirus Software: Regularly updated antivirus programs can detect and remove malware.
- User Awareness Training: Educating users about phishing and safe browsing practices can mitigate the risk of malware infections.
2. Ransomware

Ransomware has emerged as a formidable cybersecurity threat, targeting individuals, businesses, and even critical infrastructure. It encrypts files or locks users out of their systems until a ransom is paid, often in cryptocurrency. Recent years have seen a surge in ransomware attacks, causing widespread disruption and financial losses.
Techniques:
- Phishing: Most ransomware attacks begin with a phishing email containing malicious links or attachments.
- Remote Desktop Protocol (RDP) Exploits: Attackers exploit vulnerabilities in RDP to gain unauthorized access to networks and deploy ransomware.
- Brute Force Attacks: They attempt to guess weak passwords to access systems and initiate ransomware infections.
Impact:
- Financial Losses: Businesses may incur significant financial losses due to downtime, recovery costs, and ransom payments.
- Reputation Damage: Ransomware attacks can tarnish an organization’s reputation and erode customer trust.
- Data Loss: In some cases, even after paying the ransom, victims may not recover all of their encrypted data.
Prevention:
- Regular Backups: Maintaining up-to-date backups of critical data can mitigate the impact of ransomware attacks.
- Network Segmentation: Segmenting networks can limit the spread of ransomware within an organization.
- Patch Management: Promptly applying security patches and updates can address vulnerabilities exploited by ransomware.
3. Phishing Attacks

Phishing attacks continue to be a prevalent cybersecurity threat, relying on social engineering techniques to deceive users into divulging sensitive information or downloading malware. Despite advancements in email filtering and cybersecurity awareness, phishing remains a favored tactic among cybercriminals due to its effectiveness.
Techniques:
- Spear Phishing: Targeted phishing attacks that tailor messages to specific individuals or organizations, often using personal information obtained from social media or data breaches.
- Smishing: Phishing attacks conducted via SMS or text messages, enticing users to click on malicious links or provide personal information.
- Vishing: Voice-based phishing attacks where attackers impersonate legitimate entities over the phone to extract sensitive information.
Impact:
- Data Breaches: Successful phishing attacks can lead to the compromise of sensitive data, including login credentials and financial information.
- Identity Theft: Stolen personal information can be used for fraudulent activities or sold on the dark web.
- Reputation Damage: Organizations may suffer reputational harm if they are implicated in phishing incidents that compromise customer data.
Prevention:
- Employee Training: Regular cybersecurity awareness training can help employees recognize and report phishing attempts.
- Email Filtering: Implementing robust email filtering solutions can block phishing emails before they reach users’ inboxes.
- Multi-factor Authentication (MFA): MFA adds an extra layer of security, making it harder for attackers to compromise accounts through phishing.
4. DDoS Attacks
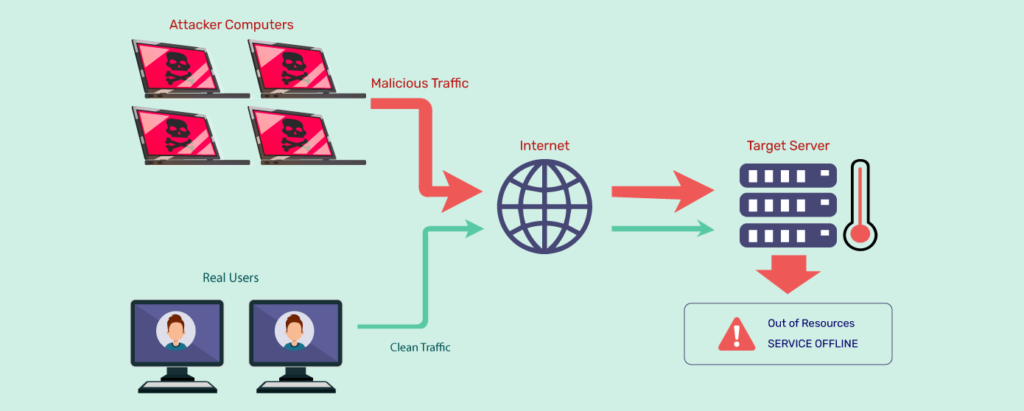
Distributed Denial of Service (DDoS) attacks pose a significant threat to online services, aiming to overwhelm servers or networks with a flood of traffic, rendering them inaccessible to legitimate users. These attacks can disrupt operations, cause financial losses, and tarnish the reputation of targeted organizations.
Techniques:
- Botnets: Attackers leverage networks of compromised devices (botnets) to launch coordinated DDoS attacks.
- Amplification: Exploiting vulnerabilities in protocols like DNS or NTP to amplify the volume of traffic directed at the target.
Impact:
- Service Disruption: DDoS attacks can render websites and online services unavailable to users, leading to downtime and lost revenue.
- Financial Losses: Organizations may incur costs associated with mitigating the attack and restoring services.
- Reputation Damage: Prolonged DDoS attacks can damage the reputation of businesses and erode customer trust.
Prevention:
- DDoS Mitigation Services: Employing specialized DDoS mitigation services or appliances can help detect and mitigate attacks in real-time.
- Traffic Scrubbing: Filtering incoming traffic to remove malicious packets before they reach the target infrastructure.
- Capacity Planning: Ensuring sufficient network capacity to absorb sudden spikes in traffic can mitigate the impact of DDoS attacks.
5. Insider Threats
Insider threats refer to the risks posed by individuals within an organization who misuse their access privileges to compromise security. While external cyber threats often receive more attention, insider threats can be equally damaging, as insiders may have knowledge of sensitive data and systems.
Types:
- Malicious Insiders: Intentional actions by employees, contractors, or partners to harm the organization, steal data, or sabotage systems.
- Negligent Insiders: Unintentional actions or errors that result in security breaches, such as falling victim to phishing or mishandling sensitive information.
Impact:
- Data Theft: Malicious insiders may exfiltrate sensitive data for personal gain or to sell to external parties.
- System Sabotage: Insiders with privileged access can disrupt operations, delete critical data, or install malware.
- Compliance Violations: Insider actions that lead to data breaches or non-compliance with regulations can result in legal consequences and fines.
Prevention:
- Access Control: Implementing the principle of least privilege and regularly reviewing user access rights can limit the potential damage from insider threats.
- Employee Monitoring: Monitoring user activity and behavior can help detect suspicious or anomalous actions indicative of insider threats.
- Security Awareness Training: Educating employees about security best practices and the consequences of insider threats can mitigate the risk of insider incidents.
6. Zero-Day Exploits

Zero-day exploits are cybersecurity vulnerabilities that are actively exploited by attackers before the software vendor releases a patch or fix. These vulnerabilities pose a significant risk as they leave systems vulnerable to attacks without any available defense or mitigation measures.
Characteristics:
- Unpatched Vulnerabilities: Zero-day exploits target vulnerabilities for which no patch or fix is available.
- Stealthy: Attackers often use zero-day exploits to infiltrate systems undetected, as traditional security measures may not recognize the exploit.
Impact:
- Data Breaches: Attackers can exploit zero-day vulnerabilities to gain unauthorized access to sensitive data.
- Targeted Attacks: Zero-day exploits are often used in targeted attacks against high-value individuals, organizations, or governments.
- Reputation Damage: Organizations may face reputational harm if they are unable to quickly mitigate zero-day exploits and protect customer data.
Prevention:
- Vulnerability Management: Implementing robust vulnerability management processes can help identify and patch zero-day vulnerabilities promptly.
- Threat Intelligence: Monitoring threat intelligence sources can provide early warning of emerging zero-day exploits and inform defensive strategies.
- Behavioral Analysis: Utilizing behavioral analysis techniques can help detect and mitigate zero-day exploits that evade traditional signature-based defenses.
Conclusion
In conclusion, the top cybersecurity threats facing the internet today represent a complex and constantly evolving landscape of risks and challenges. From malware and ransomware to phishing attacks and DDoS assaults, organizations and individuals must remain vigilant and proactive in their cybersecurity efforts. By understanding these threats, implementing robust security measures, and staying informed about emerging risks, we can collectively defend against cyber threats and safeguard the integrity and security of the digital world.